Ransomware Cyber-Attack:
A cyber-attack that has hit 150 countries since Friday should be treated by governments around the world as a "wake-up call", Microsoft says.
It blamed governments for storing data on software vulnerabilities which could then be accessed by hackers.
It says the latest virus exploits a flaw in Microsoft Windows identified by, and stolen from, US intelligence.
There are fears of more "ransomware" attacks as people begin work on Monday, although few have been reported so far.
Many firms have had experts working over the weekend to prevent new infections. The virus took control of users' files and demanded $300 (£230) payments to restore access.
The spread of the virus slowed over the weekend but the respite might only be brief, experts have said. More than 200,000 computers have been affected so far.
- Is my computer at risk?
- Blogger halts ransomware 'by accident'
- How roots can be traced to the US
- 'Use NHS wisely' amid cyber-attack
But on Monday South Korea said just nine cases of ransomware had been found, giving no further details.
Australian officials said so far only three small-to-medium sized businesses had reported being locked out of their systems while New Zealand's ministry of the business said a small number of unconfirmed incidents were being investigated.
In Japan, both Nissan and Hitachi reported some units had been affected, while in China energy giant PetroChina said that at some petrol stations customers had been unable to use its payment system.
'Like stealing Tomahawks'
A statement from Microsoft president and chief legal officer Brad Smith on Sunday criticised the way governments store up information about security flaws in computer systems.
"We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world," he wrote.
"An equivalent scenario with conventional weapons would be the US military having some of its Tomahawk missiles stolen."
He added: "The governments of the world should treat this attack as a wake-up call."
The organization also said that many organizations had failed to keep their systems up to date, allowing the virus to spread.
Microsoft said it had released a Windows security update in March to tackle the problem involved in the latest attack, but many users were yet to run it.
"As cybercriminals become more sophisticated, there is simply no way for customers to protect themselves against threats unless they update their systems," Mr Smith said.
Analysis:
There are going to be some tough questions on Monday for those institutions which didn't do enough to keep their networks secure, as well as the organizations that were best placed to stop it happening in the first place - the NSA and Microsoft.
The NSA keeps a chest of cyber weapons to itself so it can hit targets, but Microsoft has long argued that this is dangerous. If there is a flaw in Windows, the company said, surely the safest thing to do is to let its team know straight away so it can be fixed.
But then Microsoft also needs to consider what obligation it has to update all users - not just the ones who pay extra for security on older systems.
Updating your computer if you're an individual is a piece of cake, but for a network the size of Britain's National Health Service?
Tough - time-consuming, expensive and complex.
For a company like Microsoft to say it won't keep those systems safe unless they shell out more money, then that in itself is something of a ransom.
Meanwhile, Europol's chief told the BBC the ransomware was designed to allow "infection of one computer to quickly spread across the networks", adding: "That's why we're seeing these numbers increasing all the time."
Although a temporary fix earlier slowed the infection rate, the attackers had now released a new version of the virus, he said.
A UK security researcher known as "MalwareTech", who helped to limit the ransomware attack, predicted, "another one coming... quite likely on Monday".
MalwareTech, who wants to remain anonymous, was hailed as an "accidental hero" after registering a domain name to track the spread of the virus, which actually ended up halting it.
Becky Pinkard, from Digital Shadows, a UK-based cyber-security firm, told AFP news agency that it would be easy for the initial attackers or "copy-cat authors" to change the virus code so it is difficult to guard against.
"Even if a fresh attack does not materialize on Monday, we should expect it soon afterward," she said.
In England, 48 National Health Service (NHS) trusts reported problems at hospitals, doctor surgeries or pharmacies, and 13 NHS organizations in Scotland were also affected.
Other organisations targeted worldwide included Germany's rail network Deutsche Bahn, Spanish telecommunications operator Telefonica, French carmaker Renault, US logistics giant FedEx and Russia's Interior Ministry.
Massive Ransomeware attack...Total 74 countries affected...Please do not open any email which has attachments with "tasksche.exe" file. Please send this important message to all your computer users
By now all of we have heard of the global ransomware attack. It has created a lot of confusions in the mind of computer users. Over 60,000 companies of more than 100 countries have become the victim of this malware. So how this ransomware works and what are the possible solutions......
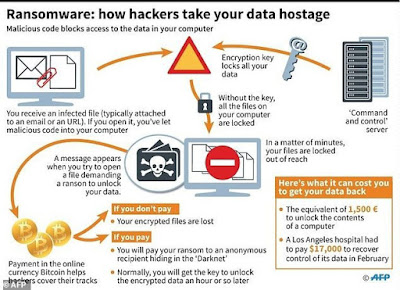
The term 'RANSOMWARE' itself gives the idea of its nature. It is somehow related to some kind of ransom. Yes, exactly it is. It is a type of malware which gets into your computer and locks down all the files. Afterwards it seeks for money from the user in order to get access to the locked files. The recent ransomwares are smarter than ever. It just not only locks down the files rather it encrypts the files which makes it really impossible to crack open the locked files. As a result the users do not have any other way to regain access to their locked files but to pay the money and get the decryption code.
So how does it get into your computer..???
The easiest to get into someone's computer is through attachments of spam emails or by entering into any unknown link. The extension of these files are different than the conventional files. Usually users turn off the file extensions, so they can not know what kind of file they are clicking on. The virus file pretends like a doc file or any other text file. But if you turn on the file extension of your computer you will see that the file extensions are different. As you click on the file all your data start encrypting and eventually asking you for ransom.
In case if you are interested these are the possible real extensions of ransomware files......( .ecc, .ezz, .exx, .zzz, .xyz, .aaa, .abc, .ccc, .vvv, .xxx, .ttt, .micro, .crypto, _crypt, .crinf, .r5a, .XRNT, .XTBL, .crypt, .R16M01D05, .pzdc, .good, .LOL!, .OMG!, .RDM, .RRK, .encryptedRSA, .crjoker, .EnCiPhErEd, .LeChiffre, .keybtc@inbox_com, .0x0, .bleep, .1999, .vault, .HA3, .toxcrypt, .magic, .SUPERCRYPT, .CTBL, .CTB2, .locky or 6-7 length extension consisting of random characters.)
The recent ransomware which is causing mass loss is known as #WannaCry. This asks for opening a javascript file in your email in the format (.js). So it is now recommended not to open any unknown attachments sent through emails.
How to recover a ransomware infected computer........?
Well, for now there is no way to open the encrypted files. As I mentioned earlier you have to pay through bitcoins in order to get the decryption code.
Safety measures :
1. Keep your Operating System up to date.
2. Keep you Anti-Virus up to date.
3. Create back up for the most important files either in a secured hard drive or in a secured cloud storage.
4. Do not open any email attachments from unknown senders.
5. Be careful while opening and downloading from any unknowing third party websites.
Stay safe.......... :)
Massive Ransomeware attack...Total 74 countries affected...Please do not open any email which has attachments with "tasksche.exe" file. Please send this important message to all your computer users
By now all of we have heard of the global ransomware attack. It has created a lot of confusions in the mind of computer users. Over 60,000 companies of more than 100 countries have become the victim of this malware. So how this ransomware works and what are the possible solutions......
The term 'RANSOMWARE' itself gives the idea of its nature. It is somehow related to some kind of ransom. Yes, exactly it is. It is a type of malware which gets into your computer and locks down all the files. Afterwards it seeks for money from the user in order to get access to the locked files. The recent ransomwares are smarter than ever. It just not only locks down the files rather it encrypts the files which makes it really impossible to crack open the locked files. As a result the users do not have any other way to regain access to their locked files but to pay the money and get the decryption code.
So how does it get into your computer..???
The easiest to get into someone's computer is through attachments of spam emails or by entering into any unknown link. The extension of these files are different than the conventional files. Usually users turn off the file extensions, so they can not know what kind of file they are clicking on. The virus file pretends like a doc file or any other text file. But if you turn on the file extension of your computer you will see that the file extensions are different. As you click on the file all your data start encrypting and eventually asking you for ransom.
In case if you are interested these are the possible real extensions of ransomware files......( .ecc, .ezz, .exx, .zzz, .xyz, .aaa, .abc, .ccc, .vvv, .xxx, .ttt, .micro, .crypto, _crypt, .crinf, .r5a, .XRNT, .XTBL, .crypt, .R16M01D05, .pzdc, .good, .LOL!, .OMG!, .RDM, .RRK, .encryptedRSA, .crjoker, .EnCiPhErEd, .LeChiffre, .keybtc@inbox_com, .0x0, .bleep, .1999, .vault, .HA3, .toxcrypt, .magic, .SUPERCRYPT, .CTBL, .CTB2, .locky or 6-7 length extension consisting of random characters.)
The recent ransomware which is causing mass loss is known as #WannaCry. This asks for opening a javascript file in your email in the format (.js). So it is now recommended not to open any unknown attachments sent through emails.
How to recover a ransomware infected computer........?
Well, for now there is no way to open the encrypted files. As I mentioned earlier you have to pay through bitcoins in order to get the decryption code.
Safety measures :
1. Keep your Operating System up to date.
2. Keep you Anti-Virus up to date.
3. Create back up for the most important files either in a secured hard drive or in a secured cloud storage.
4. Do not open any email attachments from unknown senders.
5. Be careful while opening and downloading from any unknowing third party websites.
Stay safe.......... :)




Attack Full Movie Free Download Watch Online 9xmovies
ReplyDeleteVery informative really good piece of information that save my time if you want read more about this just visit Ransomware
ReplyDeleteYou have a good point here!I totally agree with what you have said!!Thanks for sharing your views...hope more people will read this article!!! Business Model
ReplyDeleteThis is such a great resource that you are providing and you give it away for free. I love seeing blog that understand the value of providing a quality resource for free. cyberattack simulation
ReplyDeleteI have been checking out a few of your stories and i can state pretty good stuff. I will definitely bookmark your blog. enterprise cybersecurity
ReplyDeleteThanks for sharing this information. I really like your blog post very much. You have really shared a informative and interesting blog post with people.celebrities net worth
ReplyDelete